The facility to connect actions to alerts makes this an IPS. Host-based Intrusion Detection Systems HIDS Host-based intrusion detection systems also known as host intrusion detection systems or host-based IDS examine events on a computer on your network rather than the traffic that passes around the systemThis type of intrusion detection system is abbreviated to HIDS and it mainly operates by looking at data in.
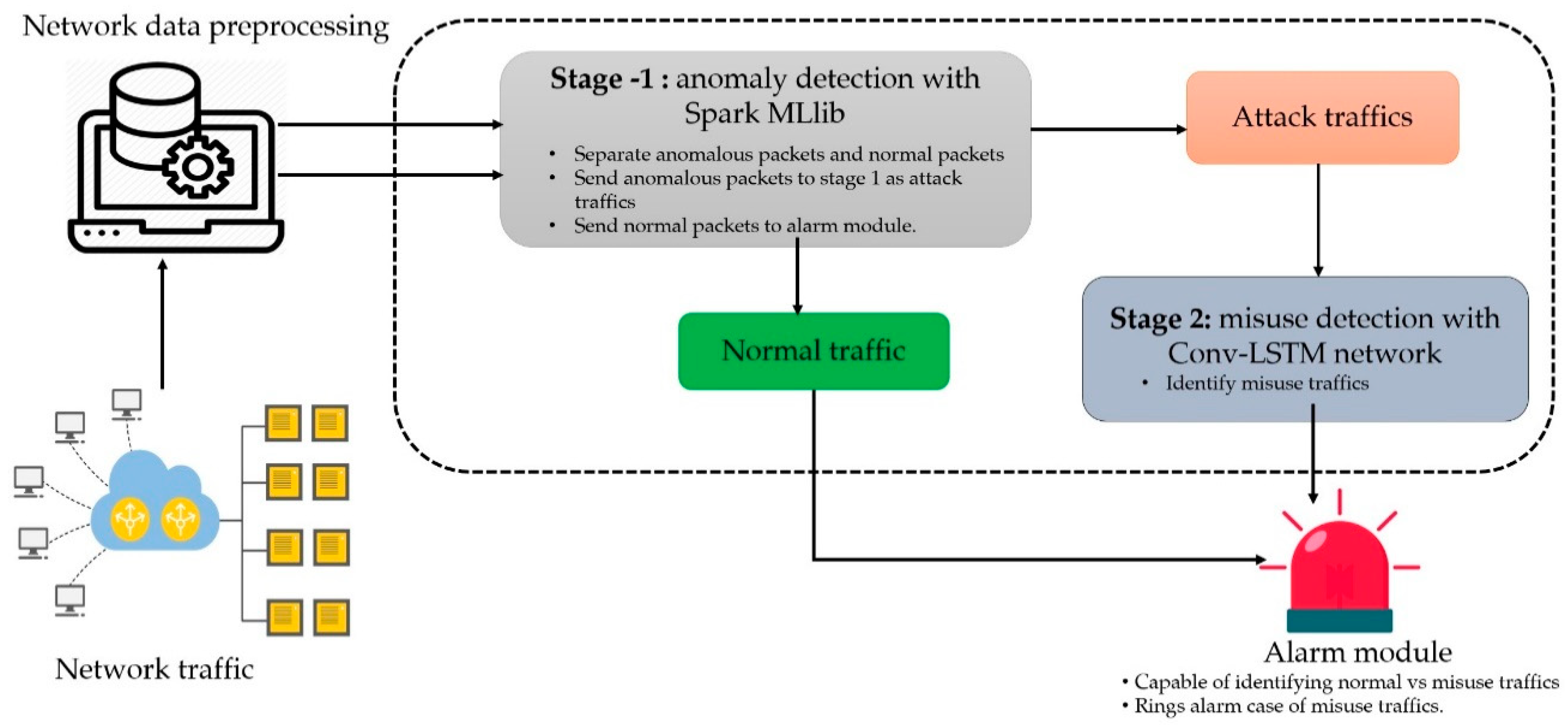
Symmetry Free Full Text A Scalable And Hybrid Intrusion Detection System Based On The Convolutional Lstm Network Html
However they differ significantly in their purposes.

Anomaly detection vs intrusion detection. For instance outbound URLs of Web activity might be. Also called behavior-based these solutions track activity within the specific scope see above looking for instances of malicious behavior at least as they define it which is a difficult job and sometimes leads to false positives. Anomaly Detection is the technique of identifying rare events or observations which can raise suspicions by being statistically different from the rest of the observations.
Thomas Dietterich and his team at Oregon State University explain how anomaly detection will occur under three different settings. This module enhances the anomaly detection rules with AI and includes more executable actions for intrusion remediation. There are two means by which HIDSs and NIDSs do the actual intrusion detection on your systems.
INTRODUCTION Video Anomaly Detection is the process of detecting abnormal events in the Video. Jan 20 2022 We will create the Python script for object detection using deep neural network with OpenCV 3. Such anomalous behaviour typically translates to some kind of a problem like a credit card fraud failing machine in a server a cyber attack etc.
The cost to get an anomaly detector from 95 detection to 98 detection could be a few years and a few ML hires. And a smooth strip of sand for. It uses opencvs readNet method and uses the external yolov3-tiny model which can be upgraded to the full sized model.
The package aims to cover both online and offline detectors for tabular data text images and time series. Anomaly-based detection looks for unusual or irregular activity caused by users or processes. About 9095 of the barrier will be constructed as a multi-layered fence system with the Israeli Defense Forces preferred design having three fences with pyramid-shaped stacks of barbed wire on the two outer fences and a lighter-weight fence with intrusion detection equipment in the middle.
Intrusion Detection Systems and firewalls are both cybersecurity solutions that can be deployed to protect an endpoint or network. Patrol roads on both sides. For more background on the importance of monitoring outliers and.
Alibi Detect is an open source Python library focused on outlier adversarial and drift detection. An IDS is a passive monitoring device that detects potential threats and generates alerts enabling security operations center analysts or incident responders to investigate and. Sagan is a free intrusion detection software system that has script execution capabilities.
Each type of IDS can employ either strategy which gives each option certain advantages. Anomaly detection in three settings In a 2018 lecture Dr. Anomaly-based intrusion detection techniques.
The main detection methods of Sagan involve the monitoring of. Both TensorFlow and PyTorch backends are supported for drift detection.

Firewall And Ips Network Intrusion Prevention System Security Solutions Deep Packet Inspection

Pdf A Survey On Anomaly And Signature Based Intrusion Detection System Ids Semantic Scholar
Signature Based Vs Anomaly Based Methods Of Intrusion Detection Download Scientific Diagram

Anomaly Based Intrusion Detection Systems The Requirements Methods Measurements And Datasets Hajj 2021 Transactions On Emerging Telecommunications Technologies Wiley Online Library

Different Anomaly Detection Modes Depending On The Availability Of Download Scientific Diagram
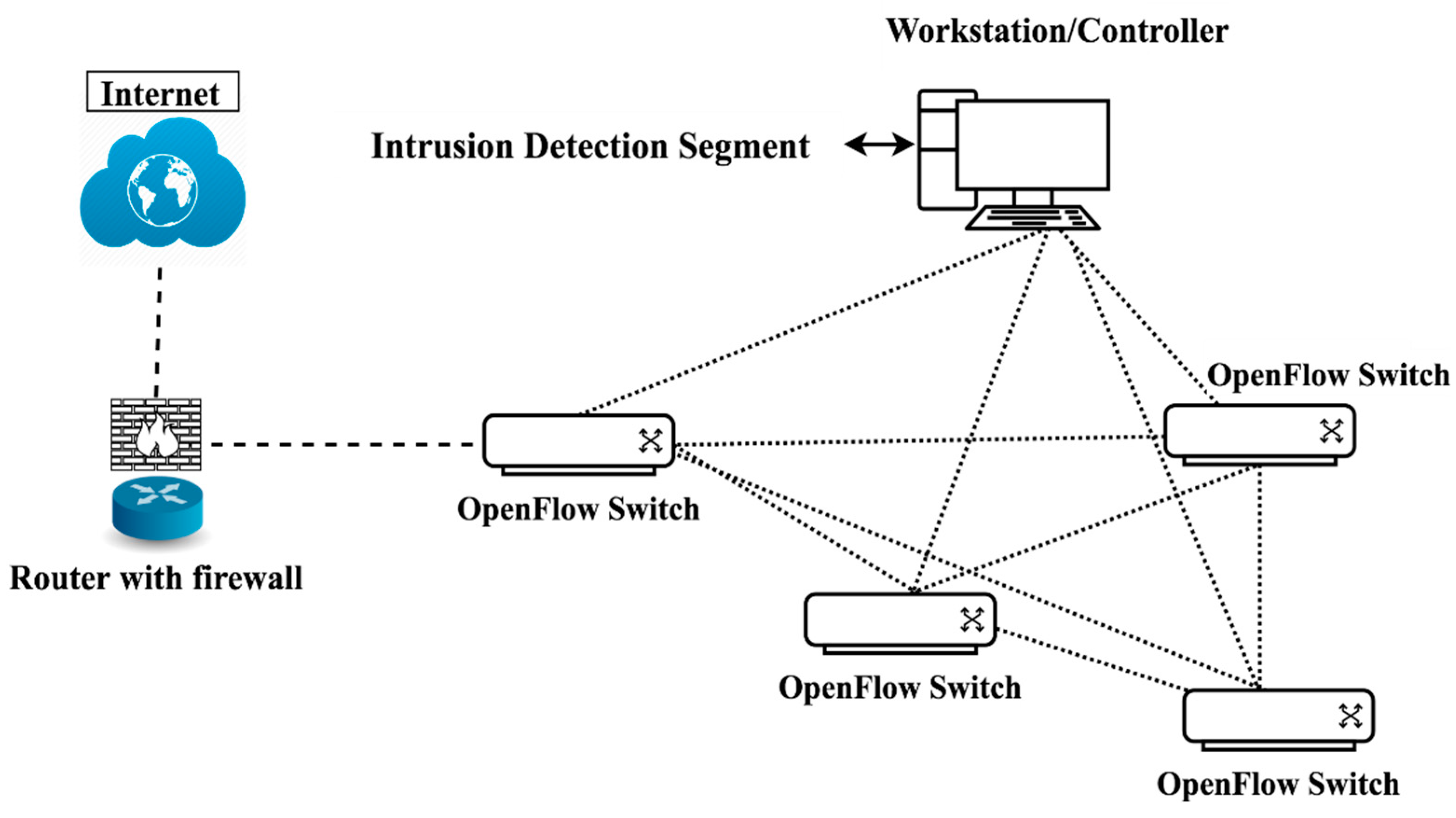
Symmetry Free Full Text Effects Of Machine Learning Approach In Flow Based Anomaly Detection On Software Defined Networking Html

Network Traffic Analysis And Anomaly Detection Scheme Using The Download Scientific Diagram

Basic Idea Of A Cooperative Anomaly And Intrusion Detection System Download Scientific Diagram

A Anomaly Based Intrusion Detection System B Signature Based Download Scientific Diagram